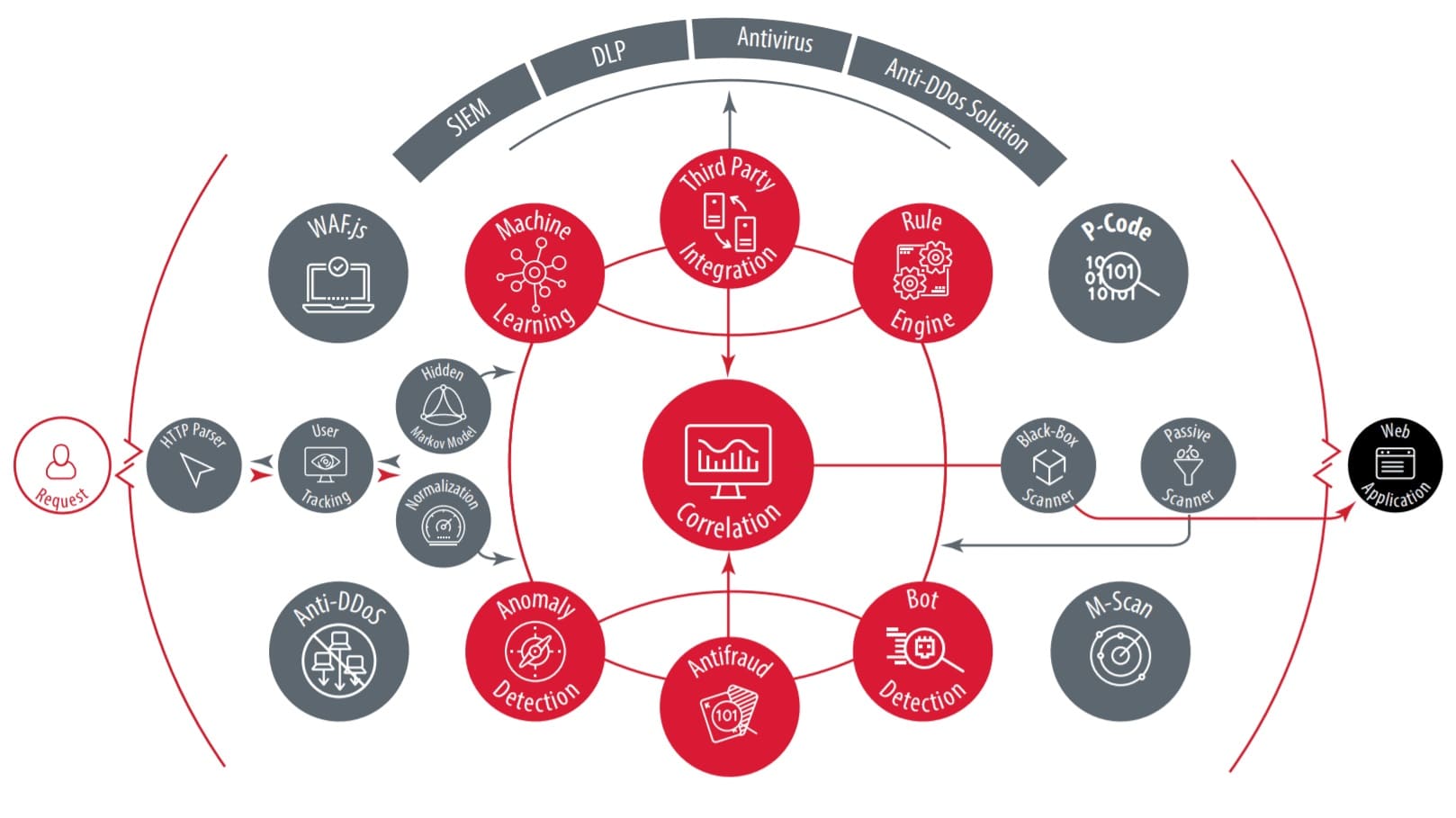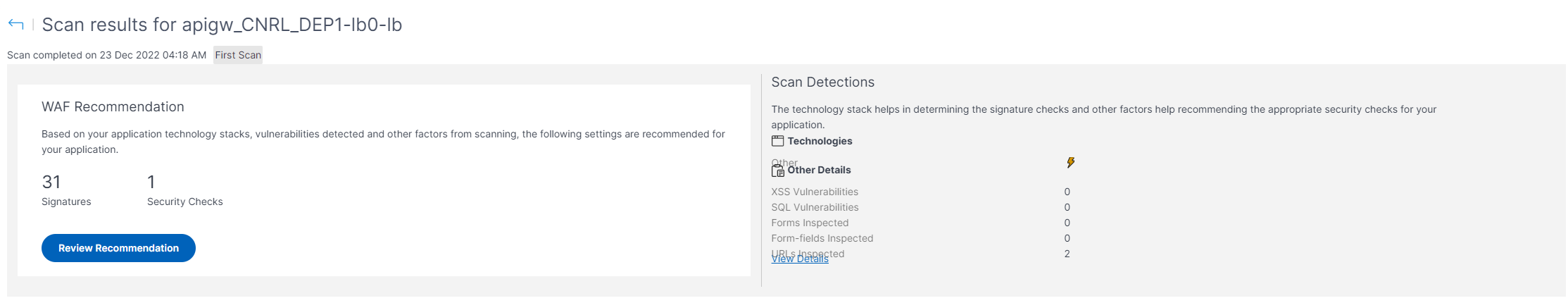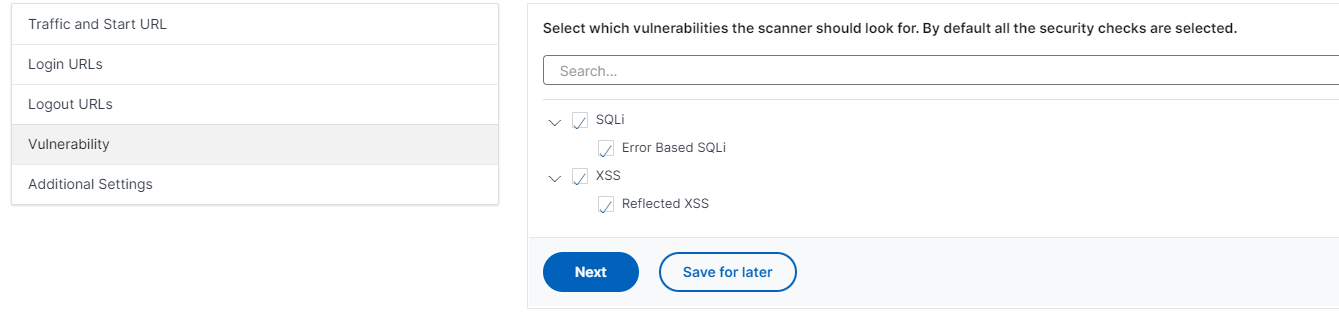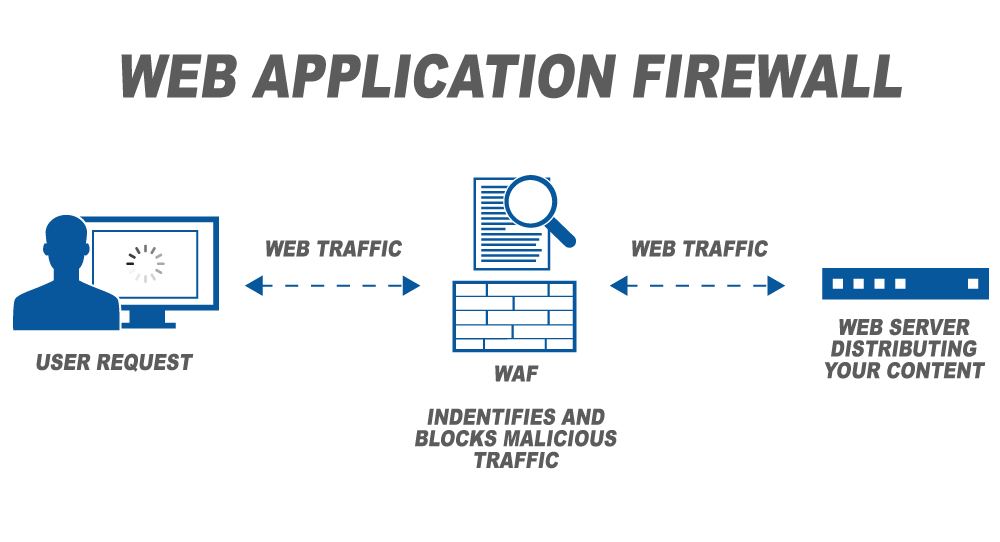
How to detect and identify the type of Web Application Firewall (WAF) - Ethical hacking and penetration testing

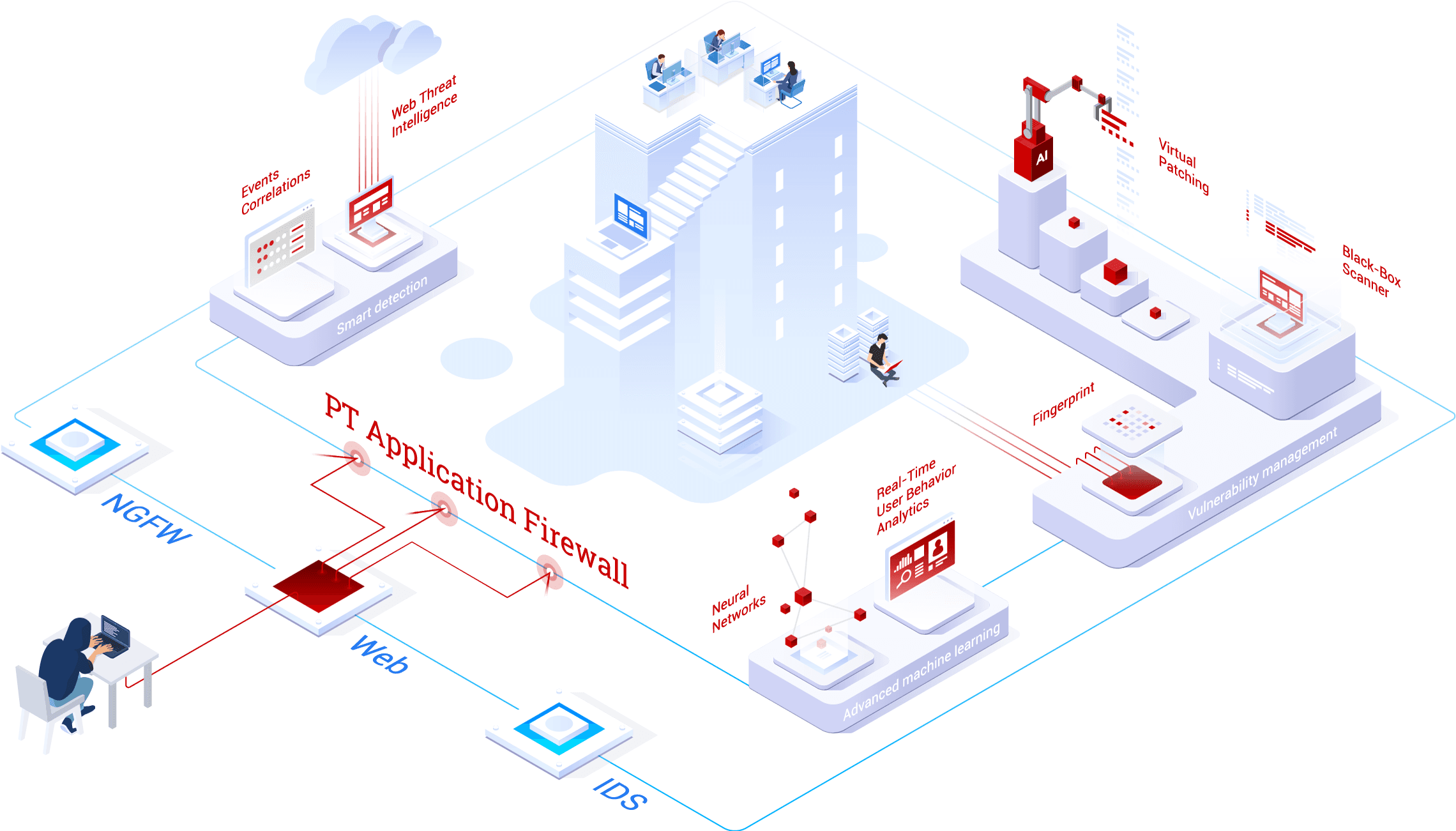
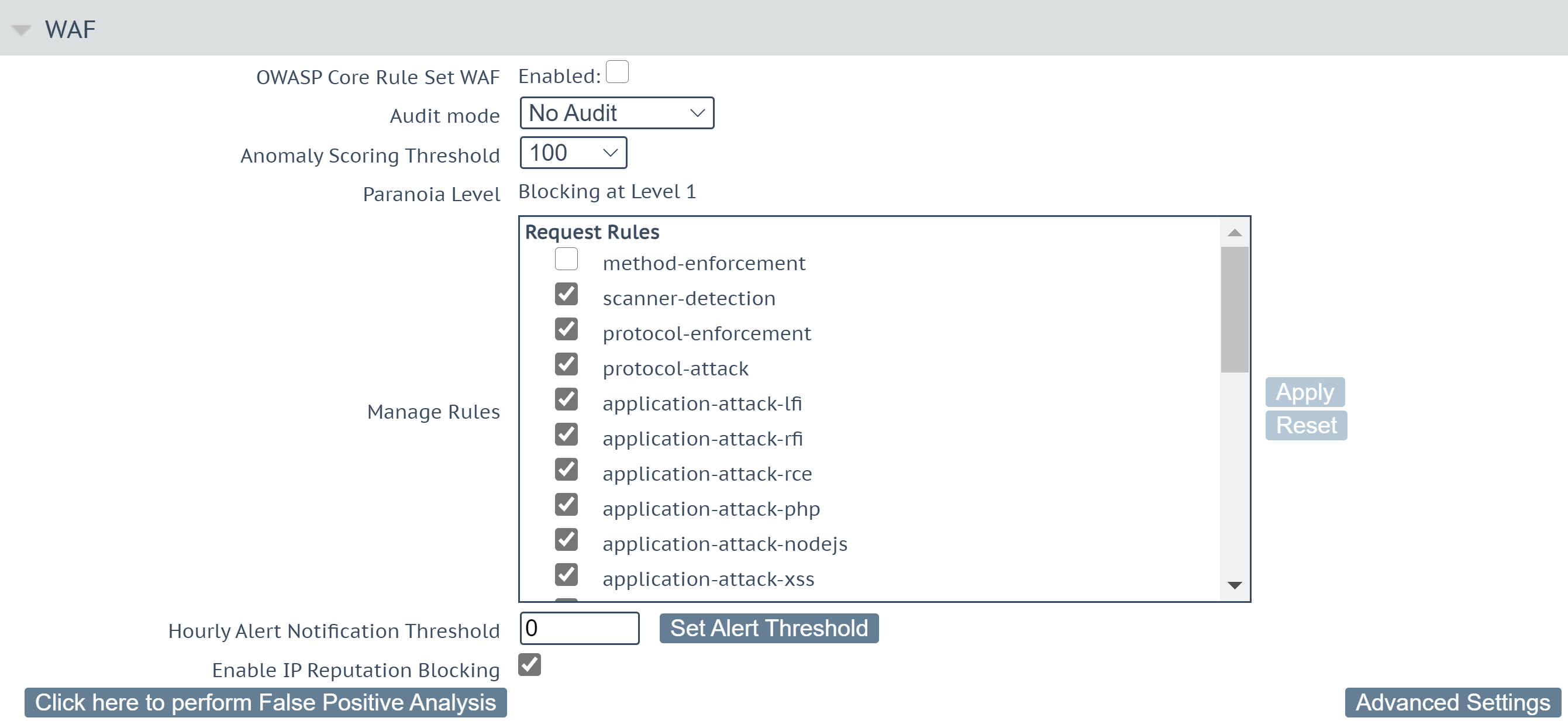
Part 2 - Reconnaissance Playbook: Azure WAF Security Protection and Detection Lab - Microsoft Tech Community

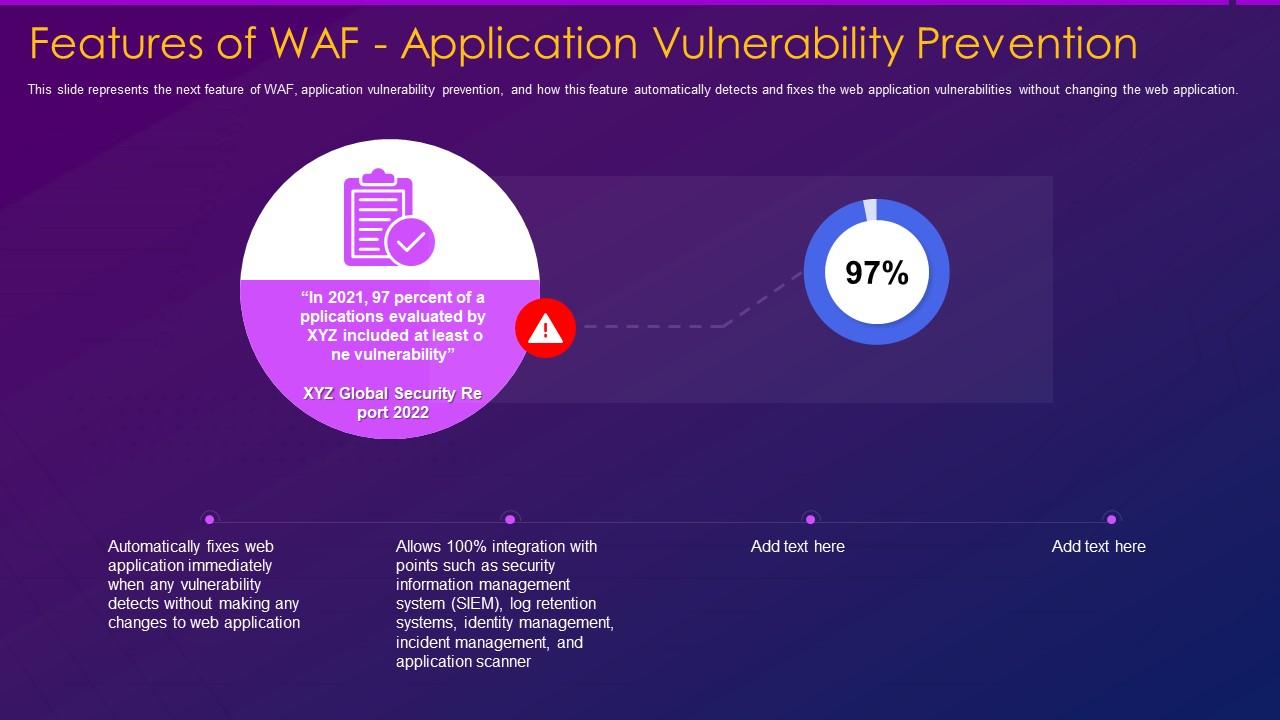
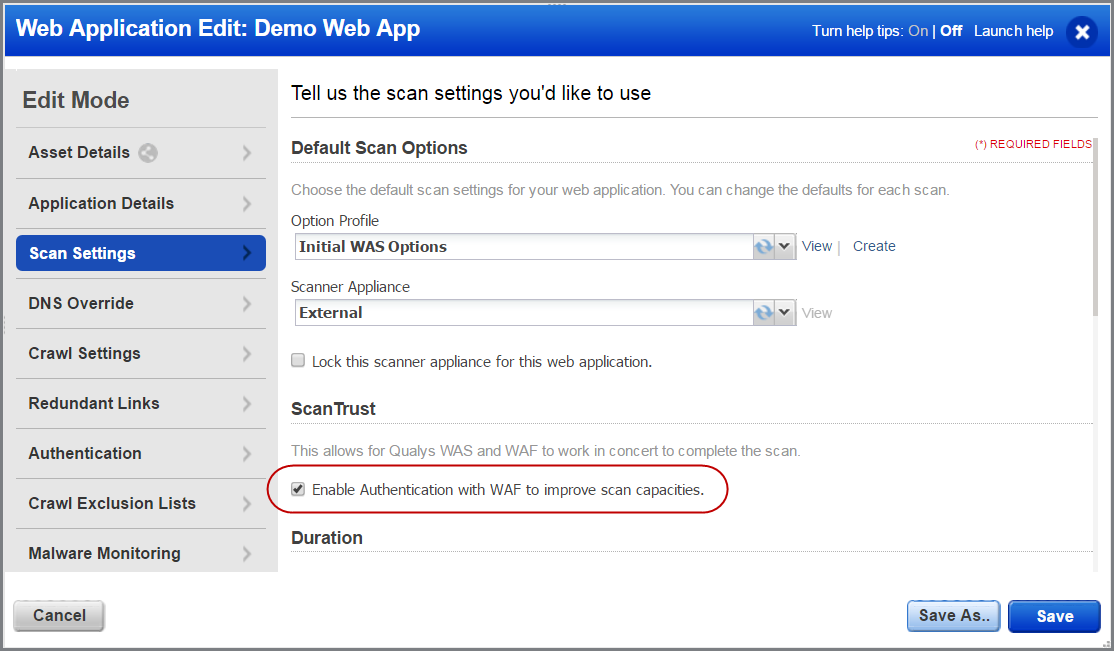
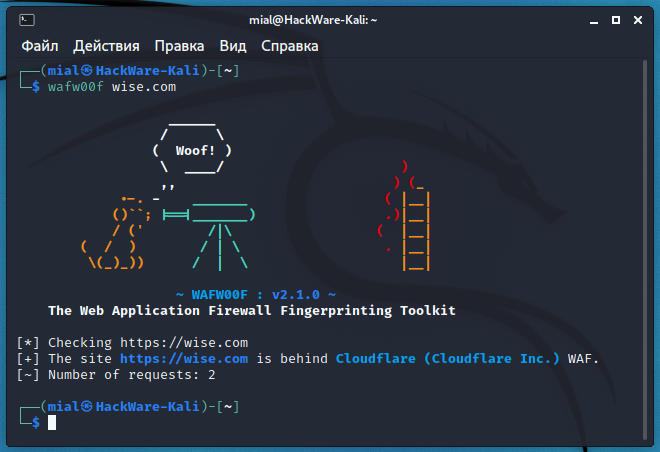
How to Protect Your Website with Web Vulnerability Scanner (WVS) and Web Application Firewall (WAF) - tech.netonboard.com