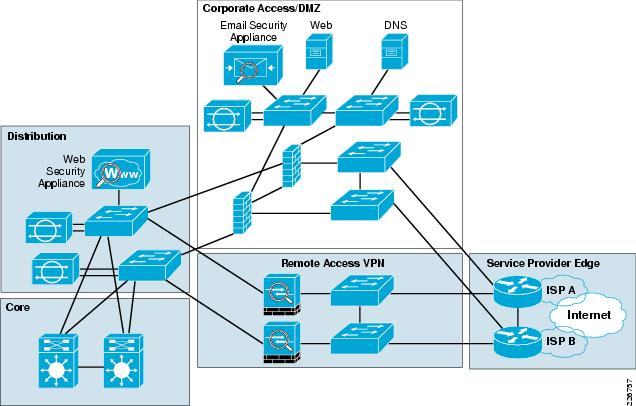
![Network Security Baseline - Getting Started with Security Baseline [Design Zone for Security] - Cisco Network Security Baseline - Getting Started with Security Baseline [Design Zone for Security] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/200001-300000/220001-230000/224001-225000/224616.eps/_jcr_content/renditions/224616.jpg)
Network Security Baseline - Getting Started with Security Baseline [Design Zone for Security] - Cisco
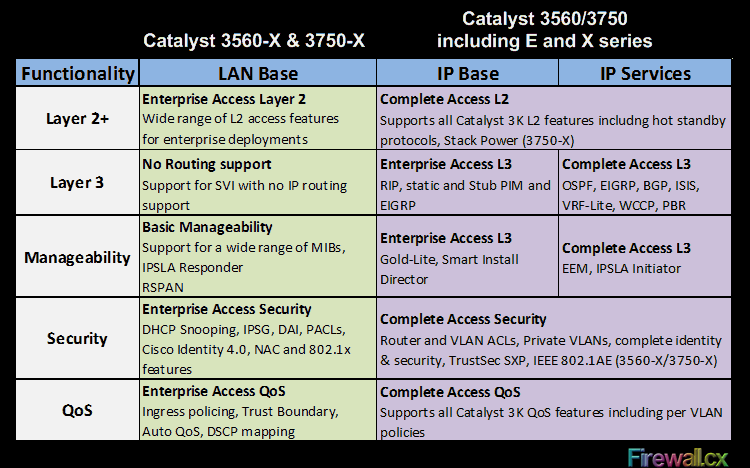
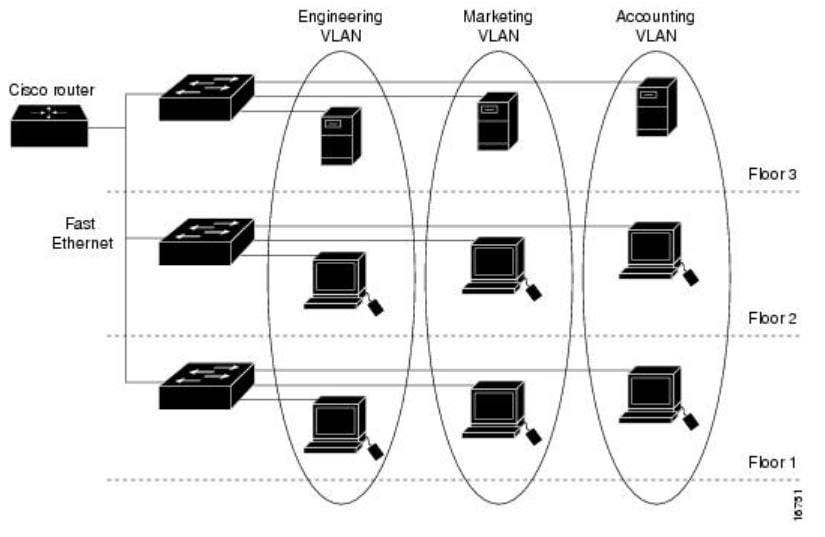
Basic & Advanced Catalyst Layer 3 Switch Configuration: Creating VLANs, InterVLAN Routing (SVI), VLAN Security, VTP, Trunk Link, NTP Configuration. IOS License Requirements for SVI Routing

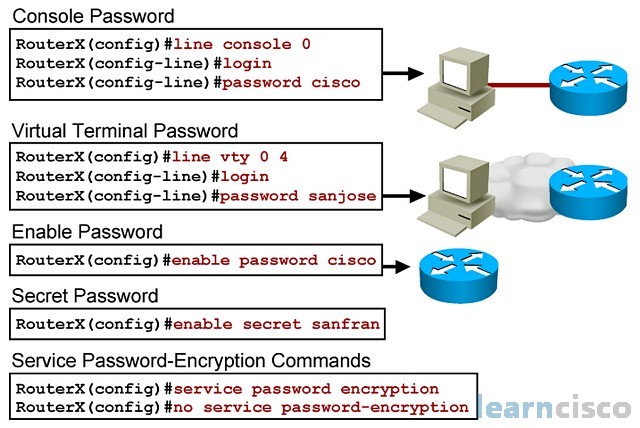
Презентация на тему: "© 2006 Cisco Systems, Inc. All rights reserved. SND v Securing LAN and WLAN Devices Mitigating Layer 2 Attacks.". Скачать бесплатно и без регистрации.


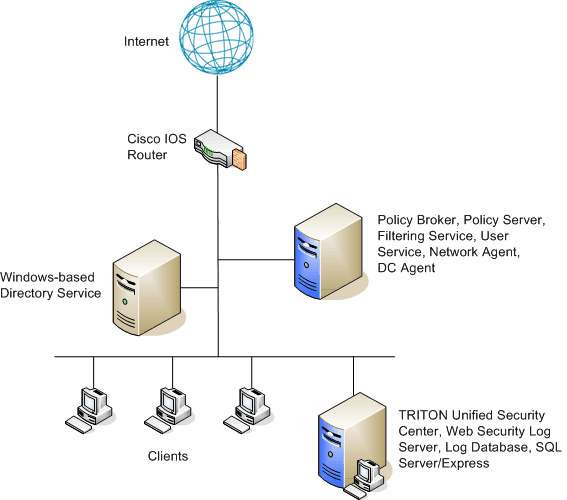
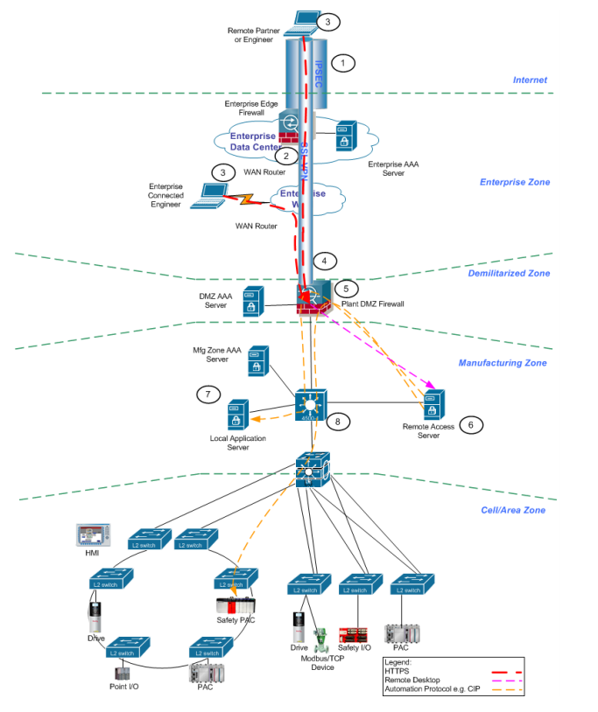
![Cisco SAFE Reference Guide - Enterprise Internet Edge [Design Zone for Security] - Cisco Cisco SAFE Reference Guide - Enterprise Internet Edge [Design Zone for Security] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/200001-300000/220001-230000/226001-227000/226754.eps/_jcr_content/renditions/226754.jpg)

![Security Best Practice to secure your Cisco Router and Switches | Learn [Solve IT] Security Best Practice to secure your Cisco Router and Switches | Learn [Solve IT]](https://i2.wp.com/techdirectarchive.com/wp-content/uploads/2020/05/980239e9-cisco-logo.jpg?fit=780%2C516&ssl=1)